Understanding cryptography even solutions manual Cryptography is the science of secret writing with the goal of hiding the meaning of a message. Cryptanalysis is science and sometimes art of. UnderstandingCryptographyOddSolutions - Solutions to understanding cryptography even solutions manual understanding cryptography even solutions Fri, 15 Feb 2019 13:33:00 GMT understanding cryptography even solutions pdf - IBM Research GmbH Zurich, Switzerland Understanding Cryptography Even Solutions - area.co.il understanding cryptography even solutions manual 'Understanding Cryptography.
Overview
Cryptography has crept into everything, from web browsers and email programs to cell phones, bank cards, cars and even into medical implants. Thus, an increasing number of people have to understand how crypto schemes work and how they can be used in practice. We wanted to create a book that teaches modern applied cryptography to readers with a technical background but without an education in pure mathematics ...
Read more »
Christof Paar
Christof Paar has the Chair for Embedded Security at the University of Bochum, Germany, and is Affiliated Professor at the University of Massachusetts at Amherst, USA. He has worked in applied cryptography since 1995. Dr. Paar has taught cryptography and security courses for 15 years to more than 1,000 students ...
Read more »
Understanding Cryptography Even Solutions Manual Pdf
Jan Pelzl
Jan Pelzl is Professor for Computer Security at the Applied University of Hamm-Lippstadt, Germany. Before becoming a Professor, he was Managing Director of ESCRYPT – Embedded Security, a leading security consultancy company. Jan Pelzl has successfully managed numerous national and international industry projects, and has a deep insight into security needs in the real world. As a researcher, Dr. Pelzl had investigated ...
Read more »
Foundations Of Cryptography - Volume 1 [goldreich]
Appendix A: Brief Background on Computational Number Theory Historical notes, suggestions for further reading,some open problems and some exercises are provided at the end of each chapter. The exercises are mostly designed to help and test the basicunderstanding of the main text, not to test or inspire creativity. The open problems are fairly well-known, still we recommend to check their current status(e.g., in this website). The work is aimed to serve both as a textbookand a reference text. That is, it is aimed at serving boththe beginner and the expert. In order to achieve this aim,the presentation of the basic material is very detailedso to allow a typical CS-undergraduate to follow it.An advanced student (and certainly an expert)will find the pace (in these parts) way too slow. However, an attempt was made to allow the latter readerto easily skip details obvious to him/her.In particular, proofs are typically presented in a modular way.We start with a high-level sketch of the main ideas,and only later pass to the technical details.Passage from high-level descriptions to lower level details istypically marked by phrases such as details follow. More advanced material is typically presented at a faster paceand with less details. Thus, we hope that the attempt to satisfy a wide range of readerswill not harm any of them. The material presented in this work is, on one hand, way beyond whatone may want to cover in a course, and on the other hand falls very short of what one may want to know about Cryptography in general.To assist these conflicting needs we make a distinction betweenbasic and advanced material, and provide suggestions for further reading (in the last section of each chapter). In particular, sections, subsections, and subsubsections marked by an asterisk (*)Continue reading >>
Institute For Advanced Study
Institute Scholars Receive Persian Heritage Foundation Grant to Study Zaydism in Iran It is my hope, says Sabine Schmidtke , Professor in the School of Historical Studies, that our work will help to develop a new field of study and to inspire a new generation of scholars to work on this material.IAS and the Persian Heritage Foundation (PHF) announce the award of a PHF grant to support the study of Zaydism in Iranpart of a major research project spearheaded by Schmidtke. Watch: What Is the Value of the Humanities? How We Read (and Write) Today In this public lecture, Suzanne Akbari, Professor in the School of Historical Studies,examines how we engage with literature and explores the case to be made for reading aloud. Edward Witten Elected Fellow of the American Association for the Advancement of Science Edward Witten ,Charles Simonyi Professor in the School of Natural Sciences, has been elected a Fellow of theAmerican Association for the Advancement of Science, along with Trustee Shirley M. Tilghman and seven former Members and Visitors. Watch: Robbert Dijkgraaf Advocates Frontier Research in ERC Live Debate Watch Robbert Dijkgraaf , IAS Director and Leon Levy Professor, join distinguished scientists at the European Research Councilconference in a panel debate on the role of frontier research with a view on sustainability. Eben Kirksey Receives ARC Grant to Explore The Promise of Justice Eben Kirksey , anthropologist and current Member in the School of Social Science, will embark on a three-year research project titledThe Promise of Justice, with funding announced today by the Australian Research Council.Continue reading >>
Understanding Cryptography By Christof Paar And Jan Pelzl - Chapter 2 Solutions - Ex2.4
Understanding Cryptography by Christof Paar and Jan Pelzl - Chapter 2 Solutions - Ex2.4 At first glance it seems as though an exhaustive key search is possible against an OTP system. Given is a short message, lets say 5 ASCII characters represented by 40 bit, which was encrypted using a 40-bit OTP. Explain exactly why an exhaustive key search will not succeed even though sufficient computational resources are available. This is a paradox since we know that the OTP is unconditionally secure. That is, explain why a brute-force attack does not work. Note: You have to resolve the paradox! That means answers such as The OTP is unconditionally secure and therefore a brute-force attack does not work are not valid I havent yet verified this solution independently. If you spot any mistakes, please leave a comment in the Disqus box at the bottom of the page. Even with a relatively small search space such as 40-bits, the plaintext could be any 40-bit number and the key could be any 40-bit number. As such any plaintext can produce any ciphertext, given the right key and any key can produce any ciphertext, given the right plaintext. The distribution of these inputs and outputs is also completely even (i.e. there are no statistical relationships of any kind). Another way of wording this is that each bit is encrypted with its own 1-bit key. As such all bits in the plaintext (or ciphertext) are completely unrelated to each other in terms of encryption and decryption. There is simply no way to confirm that the checked key is correct. With a brute-force attack, you need some means of knowing when youve found the correct answer. With a One Time Pad, no such method exists. With OTPs, there are no mathematical threads to pull on which unravel the system when found. This is in contrast to oContinue reading >>
As A Self-learner, What To Do With Books Providing Exercises But Not Solutions?
As a self-learner, what to do with books providing exercises but not solutions? Lately I've been reading lots of statistics books. Many of them have exercises after each chapter that I'm eager to solve, but I'm a beginner and can't solve most of them, and those that I think I can solve I can't check because there are no solutions and no solution manuals available. I think the point in providing exercises without solutions is that this way the book can be used in class, where the teacher can use them as homework assignments. However, I'm self-learning and have no teacher to ask/to correct my work. This frustrates me. I like solving stuff, but without knowing even if my solutions are correct (left alone anything beyond that) it's no fun. What is the best way to deal with this?Are there any resources on the internet where solutions for the more popular books could be found maybe? Should I trust that trying to solve them is the most instructional part anyway and let go of my childish craving for seeing my and the book's answer are identical? As with many things, it depends on the specific textbook, the field, how popular that text is (in college/university classes), and how basic the topic. For example, a very popular introductory physics textbook that's used by many schools will probably have some answer sets or even student-produced study guides or solutions than some high level text on some esoteric branch of a sub-sub-specialty of some field. Roddy Oct 3 '12 at 14:20 I think the point in providing exercises without solutions is that this way the book can be used in class, where the teacher can use them as homework assignments. Or maybe the author doesn't want to rob the readers of the fun/experience/torture of figuring stuff out for themselves. Remember: The goal is noContinue reading >>

The Matasano Crypto Challenges (pinboard Blog)
I recently took some time to work through the Matasano crypto challenges , a set of 48 practical programming exercises that Thomas Ptacek and his team at Matasano Security have developed as a kind of teaching tool (and baited hook). Much of what I know (or think I know) about security has come from reading tptacek's comments on Hacker News , so I was intrigued when I first saw him mention the security challenges a few months ago. At the same time, I worried that I'd be way out of my depth attempting them. As a programmer, my core strengths have always been knowing how to apologize to users, and composing funny tweets. While I can hook up a web template to a database and make the squigglies come out right, I cannot efficiently sort something for you on a whiteboard, or tell you where to get a monad. From my vantage point, crypto looms as high as Mount Olympus. To my delight, though, I was able to get through the entire sequence. It took diligence, coffee, and a lot of graph paper, but the problems were tractable. And having completed them, I've become convinced that anyone whose job it is to run a production website should try them, particularly if you have no experience with application security. Since the challenges aren't really documented anywhere, I wanted to describe what they're like in the hopes of persuading busy people to take the plunge. You get the challenges in batches of eight by emailing cryptopals at Matasano, and solve them at your own pace, in the programming language of your choice. Once you finish a set, you send in the solutions and Sean unlocks the next eight. (Curiously, after the third set, Gmail started rejecting my tarball as malware.) Most of the challenges take the form of practical attacks against common vulnerabilities, many of which will bContinue reading >>

Understanding_cryptography_odd_solutions - Solutions To...
Solutions to Homework Problems (Odd NumberedProblems)Understanding CryptographyA Textbook for Students and Practitionersby Christof Paar and Jan Pelzl1 2Solutions to Homework Problems (Odd Numbered Problems)Problems of Chapter 11.11. Letter frequency analysis of the ciphertext:lettercount freq [%]lettercount freq [%]A50.77N172.63B6810.53O71.08C50.77P304.64D233.56Q71.08E50.77R8413.00F10.15S172.63G10.15T132.01H233.56U243.72I416.35V223.41J487.43W477.28K497.59X203.10L81.24Y192.94M629.60Z00.002.Because the practice of the basic movements of kata is the focus andmastery of self is the essence of Matsubayashi Ryu karate do, I shalltry to elucidate the movements of the kata according to my interpretationbased on forty years of study.It is not an easy task to explain each movement and its significance,and some must remain unexplained. To give a complete explanation, onewould have to be qualified and inspired to such an extent that he couldreach the state of enlightened mind capable of recognizing soundlesssound and shapeless shape. I do not deem myself the final authority,but my experience with kata has left no doubt that the following isthe proper application and interpretation. I offer my theories in thehope that the essence of Okinawan karate will remain intact.3. Shoshin Nagamine, further reading:The Essence of Okinawan Karate-Doby Shoshin Nagamine,Tuttle Publishing, 1998.1.3One search engine costs $ 100 including overhead. Thus, 1 million dollars buy us 10,000 engines.1. key tests per second: 5108104=51012keys/secOn average, we have to check(2127keys:(2127keys)/(51012keys/sec)=3.401025sec=1.081018yearsThat is about 108=100,000,000 times longer than the age of the universe. Good luck.2. Letibe the number of Moore iterations needed to bring the search time down to 24h:1.0810Continue reading >>
Understanding Cryptography By Christof Paar And Jan Pelzl - Chapter 4 Solutions - Ex4.1
Understanding Cryptography by Christof Paar and Jan Pelzl - Chapter 4 Solutions - Ex4.1 Since May 26, 2002, the AES (Advanced Encryption Standard) describes the official standard of the US government. The evolutionary history of AES differs from that of DES. Briefly describe the differences of the AES history in comparison to DES. Outline the fundamental events of the developing process. What is the name of the algorithm that is known as AES? Which block sizes and key lengths are supported by this algorithm? This solution is verified as correct by the official Solutions for Odd-Numbered Questions manual. 1. Unlike DES, AES was now developed in secret. It was developed via a public competition by NIST. Some of the design criteria of DES (the S-boxes in particlar) were kept secret from the public to defend against cryptographic attacks which were as yet unpublished and only known to the NSA. AES was developed by allowing a public acadamic evaluation of the algorithm candidates. This appears to be the beginning of the modern consensus that an open design process produces the most secure algorithms. 2. The important dates in the development of AES were: 2nd January 1997 - Public announcement of the need for a algorithm candidates by NIST for a new Advanced Encryption Standard. 12th September 1997 - Formal request for candidate algorithms by NIST. 20th August 1998 - 15 candidate algorithms were selected by NIST. 9th August 1999 - 5 fianlist algorithms were announced. (Mars, RC6, Rijndael, Serpent, Twofish). 2nd October 2000 - NIST announced that Rijndael had been selected as the AES algorithm. 26th November 2001 - AES was formally approved as a US federal standard. 3. The Rijndael algorithm designed by a Belgian team was selected. 4. The algorithm was designed by Dr. VincenContinue reading >>
Consumers Want Payment Innovations With Security | Pymnts.com
When TSYS conducted its first consumer payments study seven years ago, the primary focus was on debit vs. credit, according to TSYS Gavin Rosenberg. The company was simply looking to gather solid information as the debit market was undergoing significant changes. Fast forward to today, Rosenberg told PYMNTS shortly after the release of TSYS seventh U.S. Consumer Payment study , and its purview has changed significantly. Legacy data on credit and debit is still important, he said, but these days, the study grew because payments and commerce have become more complex. There are a lot of other areas we have started to explore, Rosenberg said. A lot of that is based on evolving technology, topics in the marketplace, topics in the media and consumer behaviors. Theres now a lot to explore and a lot of factors that influence what we study each year. Thinking about how consumers pay today and how they will want to pay tomorrow is data TSYS needs to best serve its issuer clients who serve those customers. Its a conversation that has grown well beyond card types. This years study focuses more heavily on emerging payments, with an eye on peer-to-peer (P2P) payments and artificial intelligence (AI)-enabled personal assistants, such as Amazons Alexa and Google Home . When asked why AI was an area of interest for this years study, Rosenberg noted that on some level, it kind of had to be. The rise of the voice-activated assistant was impossible to miss. This is the topic that is being talking about; at this point, its hard to pick up a publication in tech or finance that isnt talking about this. What we can see right now is an increasing propensity in terms of people being interested in these devices and desiring to use them more and more as they become readily available, he explainedContinue reading >>
Understanding Cryptography Solutions
Solutions to Homework Problems (Odd Numbered A Textbook for Students and Practitioners 2 Solutions to Homework Problems (Odd Numbered Problems) 1. Letter frequency analysis of the ciphertext: letter count freq [%] letter count freq [%] 2. Because the practice of the basic movements of kata is the focus and mastery of self is the essence of Matsubayashi Ryu karate do, I shall try to elucidate the movements of the kata according to my interpretation It is not an easy task to explain each movement and its significance, and some must remain unexplained. To give a complete explanation, one would have to be qualified and inspired to such an extent that he could reach the state of enlightened mind capable of recognizing soundless sound and shapeless shape. I do not deem myself the final authority, but my experience with kata has left no doubt that the following is the proper application and interpretation. I offer my theories in the hope that the essence of Okinawan karate will remain intact. 3. Shoshin Nagamine, further reading: The Essence of Okinawan Karate-Do by Shoshin Nagamine, One search engine costs $ 100 including overhead. Thus, 1 million dollars buy us 10,000 engines. We round this number up to 69 assuming the number of Moore iterations is discreet. Thus, we have Note that it is extremely unlikely that Moores Law will be valid for such a time period! Thus, a 128 bit key seems impossible to brute-force, even in the foreseeable future. 1. 15 29 mod 13 2 3 mod 13 6 mod 13 2. 2 29 mod 13 2 3 mod 13 6 mod 13 3. 2 3 mod 13 2 3 mod 13 6 mod 13 4. 2 3 mod 13 2 3 mod 13 6 mod 13 Solutions to Homework Problems (Odd Numbered Problems) 3 15, 2 and -11 (and 29 and 3 respectively) are representations of the same equivalence class modulo 13 4. Elements without a multiplicative inContinue reading >>
Hill Cipher - Crypto Corner
The Hill Cipher was invented by Lester S. Hill in 1929, and like the other Digraphic Ciphers it acts on groups of letters. Unlike the others though it is extendable to work on different sized blocks of letters. So, technically it is a polygraphic substitution cipher, as it can work on digraphs, trigraphs (3 letter blocks) or theoretically any sized blocks. The Hill Cipher uses an area of mathematics called Linear Algebra , and in particular requires the user to have an elementary understanding of matrices . It also make use of Modulo Arithmetic (like the Affine Cipher ). Because of this, the cipher has a significantly more mathematical nature than some of the others. However, it is this nature that allows it to act (relatively) easily on larger blocks of letters. In the examples given, we shall walk through all the steps to use this cipher to act on digraphs and trigraphs. It can be extended further, but this then requires a much deeper knowledge of the background mathematics. Some important concepts are used throughout: Matrix Multiplication ; Modular Inverses ; Determinants of Matrices ; Matrix Adjugates (for finding inverses). To encrypt a message using the Hill Cipher we must first turn our keyword into a key matrix (a 2 x 2 matrix for working with digraphs, a 3 x 3 matrix for working with trigraphs, etc). We also turn the plaintext into digraphs (or trigraphs) and each of these into a column vector. We then perform matrix multiplication modulo the length of the alphabet (i.e. 26) on each vector. These vectors are then converted back into letters to produce the ciphertext. We shall encrypt the plaintext message 'short example' using the keyword hill and a 2 x 2 matrix. The first step is to turn the keyword into a matrix. If the keyword was longer than the 4 lettersContinue reading >>
Understanding Cryptography Even Solutions.pdf - Ebook And Manual Free Download
Understanding Cryptography Pdf
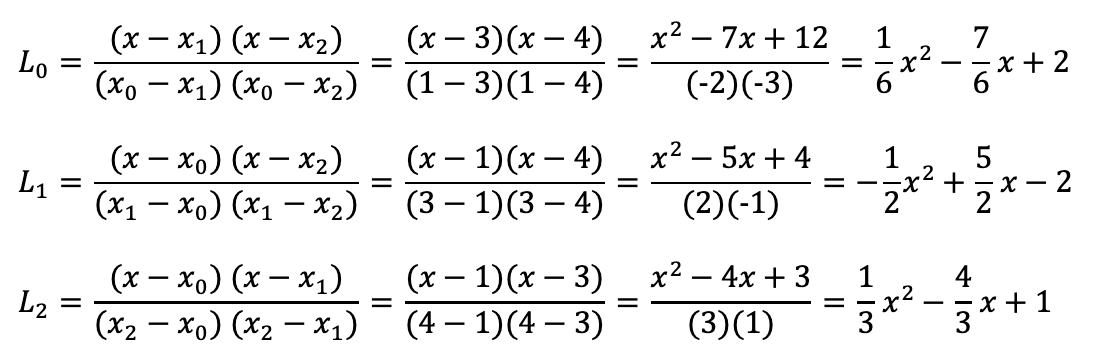
09627453.doc - Teaching Materials 1. Introduction to Cryptography, J. A. Buchmann ... . Handbook of Applied Cryptography, A. Menezes, P ... S. Vanstone 3. Introduction to Modern Cryptography, M. Bellare and ... Download our understanding cryptography even solutions eBooks for free and learn more about understanding cryptography even solutions. These books contain exercises and tutorials to improve your practical skills, at all levels! To find more books about understanding cryptography even solutions, you can use related keywords : Cryptography Forouzan Solutions Pdf, Solutions Of Cryptography And Network Security 2nd Edition By Forouzan, Download Cryptography And Network Security By Forouzan Pdf Solutions, Understanding Financial Statements 9th Edition Solutions Pdf Torrent, Understanding Engineering Mechanics Statics Pytel And Kiusalaas Pdf Solutions Ftorrents, Understanding Pathophysiology, 5e (Huether, Understanding Pathophysiology) Torrent, Cryptography 3edition Pdf, Practical Cryptography Pdf, Solutions Of Numerical Methods In Engineering And Science By B.s.grewel Solutions Pdf, Cryptography By Atul Kahate You can download PDF versions of the user's guide, manuals and ebooks about understanding cryptography even solutions, you can also find and download for free A free online manual (notices) with beginner and intermediate, Downloads Documentation, You can download PDF files (or DOC and PPT) about understanding cryptography even solutions for free, but please respect copyrighted ebooks.Continue reading >>

What Are Ways To Become An Expert In Cryptography?
Updated Jul 25, 2014 Author has 114 answers and 305.9k answer views This answer takes a look at cryptography from a theorist's perspective. To become a true expert in theoretical cryptography might take you your whole life and more. To self-start yourself on a path of understanding the latest ground-breaking results in cryptography and contribute to theoretical research yourself, the following is a good introduction. Prof. Dan Boneh runs a two part course in cryptography on Coursera. I haven't taken that course myself, but it seems pretty useful as a starting point. To supplement your knowledge, you can follow lecture notes from a variety of cryptography courses. Some of the more useful ones would be: Jonathan Katz and Yehuda Lindell's Introduction to Modern Cryptography: Principles and Protocols . Oded Goldreich's two-part Foundations of Cryptography (Volumes I and II ). Note that this work is considered slightly more technical and esoteric than others, but you will survive. Research in cryptography requires solid background in algebra (both linear and abstract), number theory and computational complexity. You might also require other areas of mathematics depending on your specialisation. The useful thing here is to keep good resources for the subjects and hand and refer to them as and when you need. There are many books and courses you can do for linear and abstract algebra, but A Computational Introduction to Number Theory and Algebra by Victor Shoup is a good resource for number theory in the cryptographic context, and Computational Complexity: A Modern Approach remains the definitive authority in the field of computational complexity. You would easily have spend a couple of years covering this material, and this would give you a very good sense of cryptography, th Continue reading >>
Information Security Interview Questions

Understanding Cryptography Even Solutions Manual Free
What follows is a list of questions for use in vetting candidates for positions in Information Security. The list has evolved over the years, as I think it should, and I think represents a good balance between technical content and the philosophy around desired answers. Perhaps the worst mistake you can make when doing technical interviews is filtering people out that you shouldnt due to fetishization of the interview process and an unfounded belief in the correlation between answers to the questions and a potential employees performance. Google figured this out many years ago , and they started focusing on scenario and behavior-based interviews instead of those based on specific (gotcha) nuggets of information. They figured out its not about asking hard things that can easily be looked up, but rather understanding how people approach problems, what their talents and interests are, and what work they have done in the past. Sadly this is not yet understood by most interviewers and HR departments, and theyre still stuck in the mode of asking magic questions and looking for their favorite pet answers. The process has been shown to be highly biased, with interviews basically looking for people who fit their particular model of good (which usually matches something like themselves). Google found that this doesnt work. It has no mapping to success as an employee whatsoever. I rely on the data more than my anecdotes, but as someone whos given many, many technical interviews, I can tell you that this is consistent with my experience. Ive hired people who are star performers that effectively failed at these questions, and we have people who crushed them and floundered once hired. The lesson here is not to avoid technical questions: Its that you need to be cautious of the tendenContinue reading >>
What Is Encryption? - Definition From Whatis.com
Contributor(s): Peter Loshin , Michael Cobb , Robert Bauchle, Fred Hazen, John Lund, Gabe Oakley, Frank Rundatz Encrypting Data at Rest Amazon Web Services In computing, encryption is the method by which plaintext or any other type of data is converted from a readable form to an encoded version that can only be decoded by another entity if they have access to a decryption key. Encryption is one of the most important methods for providing data security, especially for end-to-end protection of data transmitted across networks. Experts reveal 18 types of cryptography attacks, and how they are executed. Todays cryptography is far more advanced than the cryptosystems of yesterday, dont let your system be compromised. This email address doesnt appear to be valid. This email address is already registered. Please login . You have exceeded the maximum character limit. Please provide a Corporate E-mail Address. By submitting my Email address I confirm that I have read and accepted the Terms of Use and Declaration of Consent. By submitting your personal information, you agree that TechTarget and its partners may contact you regarding relevant content, products and special offers. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy . Encryption is widely used on the internet to protect user information being sent between a browser and a server, including passwords, payment information and other personal information that should be considered private. Organizations and individuals also commonly use encryption to protect sensitive data stored on computers, servers and mobile devices like phones or tablets. Unencrypted data, often referred to as plaintext , is eContinue reading >>
Explaining Blockchainhow Proof Of Work Enables Trustless Consensus
Software engineer with interests in social innovation, psychology, philosophy, ethics and spirituality. Co-founder @ coinfund.io and Consensus Labs, Inc. Explaining blockchain how proof of work enables trustless consensus Blockchain technology, of which Bitcoin is an example, can be quite hard to understand. Mainly this is because core concepts tend to get lost among the complexity of non-essential details. This article tries to fill the gap between general audience literature that is entirely uninformative to computer professionals and highly specialized literature that is informative, but often overwhelming. It is written for people with some technology background but without in-depth familiarity with this particular field. The subject of this article is technology of distributed trustless consensus, for this is the one area in which blockchain systems, like Bitcoin, are indeed a major breakthrough. When it comes to other goals, such as distributed data storage, anonymity, transaction verifiability, data obfuscation, shared ledgers, micropayments, high throughput, digital contracts, and so on, cryptographic blockchain systems are, essentially, incidental. Solutions to these problems are well known outside of the blockchain space and, consequently, I will not focus on them here. The main innovation that Satoshi Nakamoto introduced in his article is using so-called proof of work (POW) to create distributed trustless consensus and solve the double-spend problem. POW is not a new idea, but the way Satoshi combined this and other existing concepts cryptographic signatures, merkle chains, and P2P networks into a viable distributed consensus system, of which cryptocurrency is the first and basic application, was quite innovative. Proof of work is a requirement that expensivContinue reading >>